DSTIKE Deauther Watch Z | ESP8266 + Atmega32u4 Development Watch
Reliable shipping
Flexible returns
The Deauther Watch Z-IR version includes an additional infrared remote control compared to Deauther Watch Z. While Deauther watch Z allows only 3 buttons to execute 3 scripts, the IR version can execute 21 scripts through the remote control.Due to the use of the infrared functionality, the original three buttons have been disabled.
| Difference | Deauther Watch SE | Deauther Watch V3S | Deauther Watch V4S |
|---|---|---|---|
| New Name | Deauther Watch X | Deauther Watch Y | Deauther Watch Z |
| Battery | 500mah | 1000mah | 1000mah |
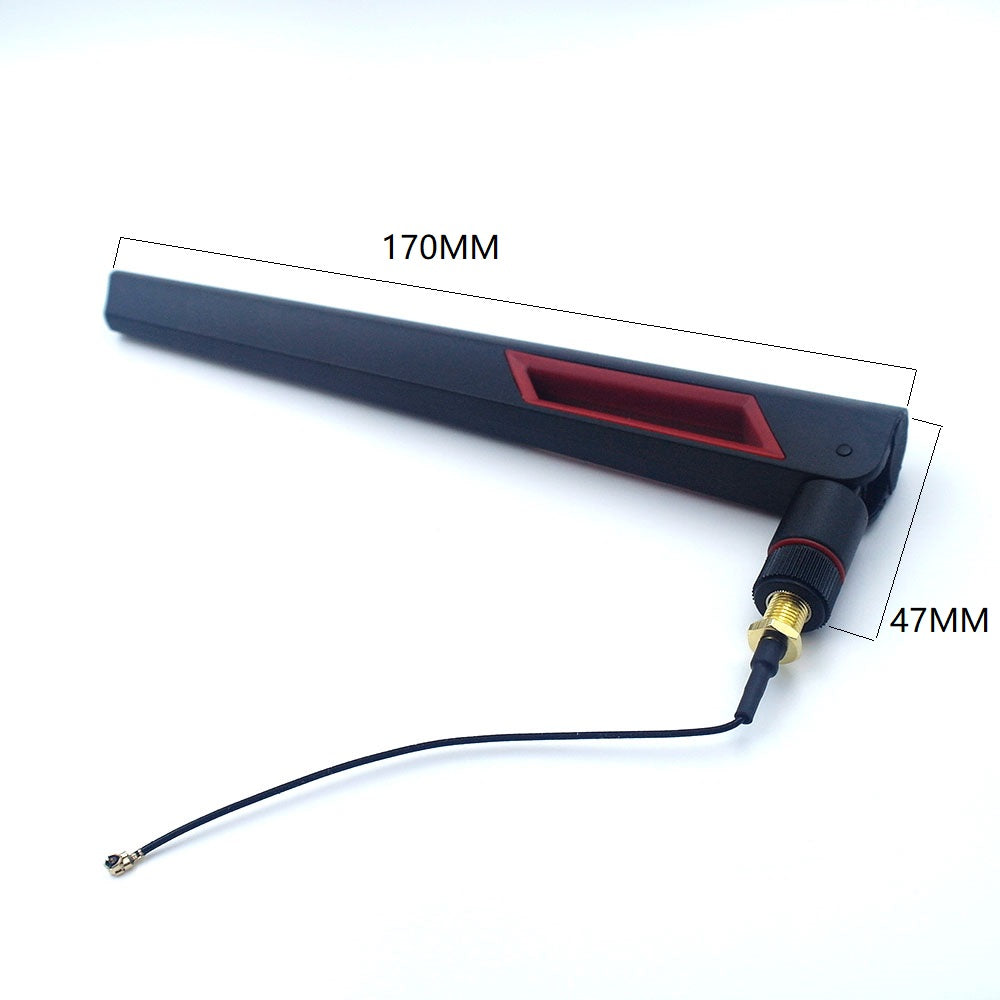
| Antenna Range | 30-50m | 80-100m | 80-100m |
| Color | Black/Green/Red | Black | Black |
| USB | Micro USB | USB-C | USB-C |
| Buzzer | YES | NO | NO |
| BadUSB | NO | NO | YES |
| TFcard | NO | NO | YES |
| Work Time | 5-6h | 9-10h | 9-10h |
| Weight | 62g | 80g | 99g |
| Size(LxWxH mm) | 60x50x25 | 80x50x25 | 80x70x25 |
What is it ?
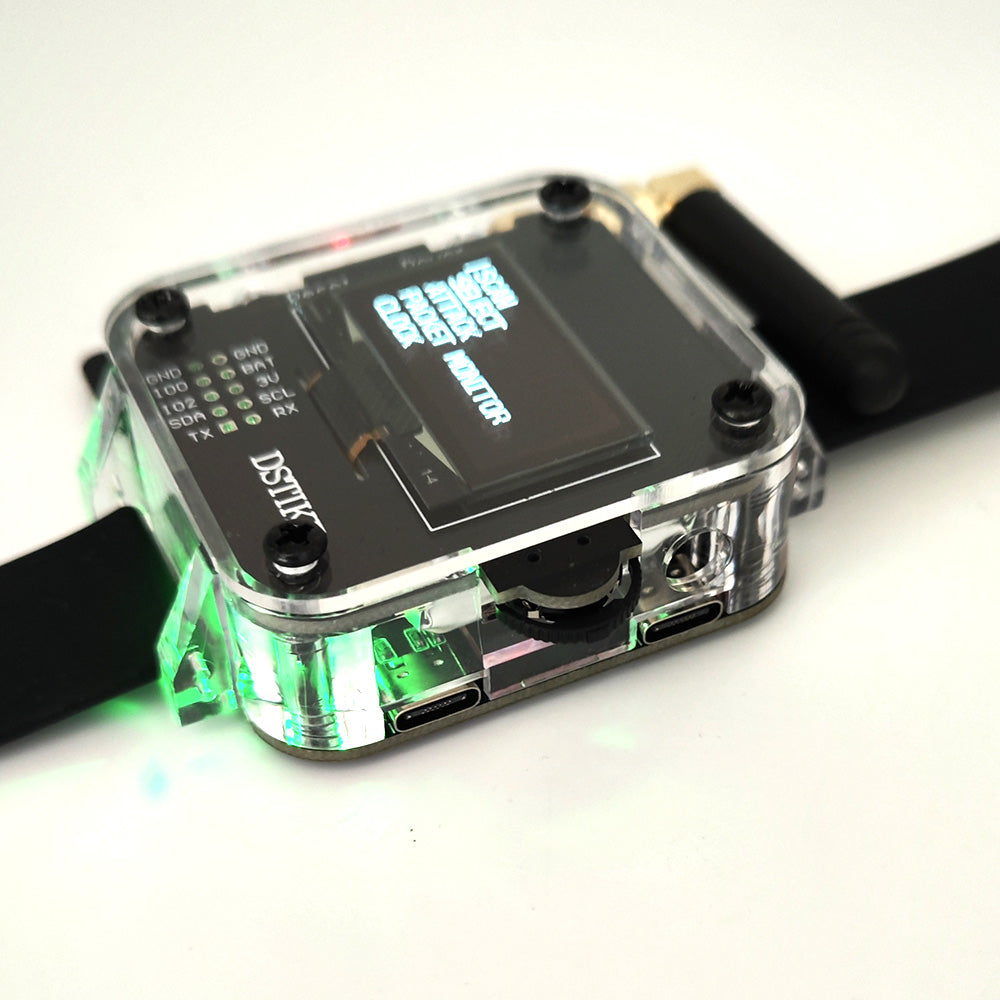
The DSTIKE Deauther Watch Z is a portable device packed with multiple functions, designed specifically for wireless network security research, WiFi testing, and convenient everyday applications. Powered by the ESP8266 chip, the Deauther Watch Z can perform WiFi network deauthentication, signal scanning, and probe request analysis, making it highly suitable for network security research and education. Additionally, with the integration of the Atmega32u4 chip, the Deauther Watch Z is capable of executing BadUSB attacks. By disguising the device as a USB keyboard, users can automatically execute predefined malicious command scripts when connected to a target computer, further enhancing the device's capabilities in network penetration testing.
All the source code is on the SD card. You can visit deauther.com to learn about deauther, visit hak5.org to learn about ducky script.
Why did you make it?
The old model requires the buyer to program Arduino themselves to execute a Bad USB attack. The new model does not require the buyer to download and install Arduino. The buyer only needs to modify the script in the txt file.
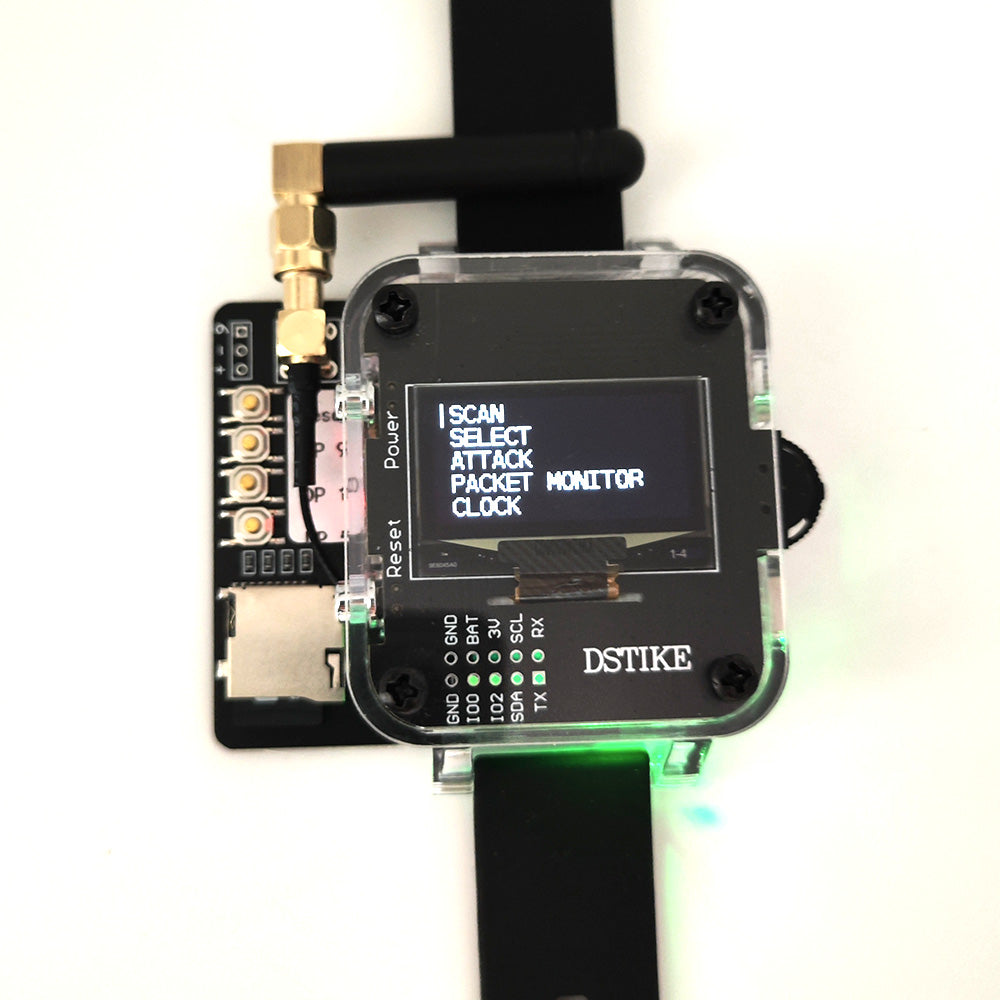
Function
- Deauther Attack: Disconnect 2.4G WiFi
- Deauther Beacon: Create fake networks
- Deauther Probe: Confuse WiFi trackers
- Packet Monitor: Display WiFi traffic
- Clock: Real Time Clock Adjustable
- Bad USB Attack: The Human Interface Device (HID) Attack
Disclaimer
This project serves as a proof of concept for testing and educational purposes. It is important to note that neither the ESP8266 nor its SDK were intended or developed for such purposes. As a result, bugs may occur. Please ensure that you only use this project against your own networks and devices. Prior to usage, it is essential to review and comply with the legal regulations pertaining to your country. We do not accept any responsibility for any actions taken with this program.
Attention
Please note that the ESP8266 does only support 2.4GHz. RTC chip inside could work after you turn off the watch. When the WiFi chip's indicator light is off, please charge it promptly. Deauther work time could be adjusted in the settings. Please read https://deauther.com/docs/category/usage carefully first.
More Info
Deauth
The deauthentication feature is designed to close the connection of WiFi devices by sending deauthentication frames to the selected access points and client devices. It's important to note that this attack is only possible because many devices do not implement the 802.11w-2009 standard, which provides protection against such attacks.
To ensure proper usage, please select only one target at a time. If you select multiple targets running on different channels and initiate the attack, the system will rapidly switch between those channels, making it difficult to reconnect to the access point hosting the web interface.
Beacon
Beacon packets are used to advertise access points. By continuously sending beacon packets out, it will look like you created new WiFi networks. You can specify the network names under SSIDs.
Probe
Probe requests are sent by client devices to ask if a known network is nearby. Use this attack to confuse WiFi trackers by asking for networks that you specified in the SSID list. It's unlikely you will see any impact by this attack with your home network.
Bad USB
A HID (Human Interface Device) attack is a type of cyberattack that leverages a device, often designed to mimic a keyboard or mouse, to exploit vulnerabilities in a computer system or network. This attack method takes advantage of the fact that most computer systems inherently trust input from HID devices, such as keyboards and mice.